How to Prevent Data Breach and What to Do After a Data Breach
- Blog
- Credit Report Identity Theft
How to Prevent Data Breach and What to Do After a Data Breach

Learn Tips, Insights, and Best Practices to Prevent, Stop, and Recover From A Data Breach.
Whether you're a consumer or a business owner, there is no escaping consumer data. The ecommerce industry gathers, processes, reports, buys, sells, stores, transfers, and crunches data every single second of the day. Falling victim to a data breach grows more likely every year. Learn how to prevent, mitigate, and recover from a data breach.
There are really two experiences of a data breach scenario- that of the company that experiences a security failure and that of the individual whose personal information is now openly accessible to digital predators. We explore both perspectives in this article, offering insight and advice for how to prevent data breach on a personal or organizational level, how to navigate the fallout of data breach information exposure, and how to recover from data breaches.
Research shows that on an individual level, consumers tend to have a surprisingly high level of disconnect or unawareness when it comes to the frequency and extent of a stolen information data breach (Now I’m a bit angry:” Individuals’ Awareness, Perception, and Responses to Data Breaches that Affected Them). They also seem to underestimate the impact of data breach on individuals. To help you get a better idea of what they are, what they entail, and how to avoid them in the first place, let’s take a closer look at data breach prevention tools, key data breach examples, and what a data breach response plan should look like.
What Does Data Breach Mean?
“Data breach” is a term used to describe the unauthorized access of private or sensitive information on a large scale. There are different types of data breaches, and while technically, a data breach can happen with analog (hard copy) files, for the most part, it is understood as the digital invasion of private or personally identifiable information (PII). For instance, a law firm data breach might involve private client files being accessed by an unauthorized source. Or, an Equifax data breach might involve private credit profiles being accessed by an unauthorized source.
It might help to think of a data breach as the large-scale equivalent of identity theft. Where identity theft tends to target a single person, a data breach lays bare the personal or sensitive information of a large (sometimes enormous) group of people simultaneously. But, much like identity theft, the information is usually disseminated to other parties for use in various criminal activities, or sometimes it is held ransom with the threat of impending harm if money isn’t paid to the wrongdoer.
Data breaches can happen internally (from within a company, organization, or agency) or externally (from someone unaffiliated with the company, organization, or agency). For instance, some high profile military data breaches occurred when employees or service personnel within the military or a government agency illegally downloaded classified information, stored it on a local drive or jump drive and removed it from a secure location. Or, just as with common identity theft schemes, sometimes a hacker is able to transgress digital security measures to illegally access a database and store or steal the private information within. We’ll take a look at a data breach 2024 list to explore some of the more recent occurrences.
However, unlike identity theft (which is always nefarious), data breaches can also be accidental, unintentional, and without a devious purpose. For instance, an employee may inadvertently disseminate the wrong files, giving unintentional public access to private files. Unfortunately, what many consumers may not realize is that even a data breach that began without ill intent, can rapidly turn into a dark web nightmare. In other words, even an innocent data breach can transform into a widespread identity theft situation in the blink of an eye.
Because of the costs of data breaches for companies and the fallout for consumers, many businesses and people have begun purchasing data breach insurance. (Keep reading below to learn more about this option.) And, in many instances of extremely harmful or particularly egregious incidents, a data breach lawsuit has become a viable recovery option.
How to Prevent a Data Breach
Unfortunately, preventing a data breach is not easy. The proliferation of digital information has meant that people across all sectors (government, healthcare, finance, private industry, retail, etc.) have been able to enjoy ease of access to critical and useful information without even having to leave their homes. This network of data has served as a resource for some, easing the flow of communications, engagement, and a variety of activities. For instance, if you need to make sure that a paycheck is deposited or pay a bill, you can do it all online. Or if you need to access healthcare records, make an appointment, renew a passport, etc., again, you can do it all online from the comfort of your own home.
But with this increase in technology-driven information storage and exchange comes the risk of unauthorized access to and dissemination of that information. For businesses, organizations, and agencies, mitigating these risks is about protecting customers, brands, and reputations and about limiting liability exposure. Let’s take a deeper dive into this issue.
How to prevent a data breach in a company
When it comes to business, preventing a data breach is among the ultimate challenges. This is particularly true for businesses that store and process massive amounts of sensitive data, like a bank, credit card company, or hospital.
To prevent a data breach in a company, it is absolutely imperative that best-in-class security resources are utilized and enforced company-wide. What does this mean specifically? It means doing things like these 8 ways to prevent data breaches:
| Do this! | Why it Matters |
|---|---|
| Designate a Chief Information Security Officer (CISO) or Chief Data Officer (CDO) | When it comes to data security, there must be a clear chain of command and a designated person who is ultimately responsible for the upkeep and implementation of data protection practices. This person may build a team of qualified staff, but having a single person with whom the buck stops is critical. In today’s world, for many businesses, this is as important a position as a CEO, CFO, COO, etc. |
| Stay current | Not only do data gathering, processing, and storing methods continuously evolve, but so do data security methods and data hacking methods. This means that staying current is a daily task. Preventing a data breach is never a one-and-done scenario. There is no such thing as achieving data security. It is an ongoing effort that never reaches an end. |
| Implement security protocols | Identifying and designing data security protocols is the beginning. But the proper planning and implementation of these protocols, along with any updates, is just as essential. Gaps in implementation are the birth place of vulnerabilities that lead to data breaches. |
| Limit access. | Not everyone needs access to everything. In the world of data management from a security perspective, this is especially true. Only give individuals, committees, groups, etc. access to exactly the thing that is needed to perform their job. Where it makes sense to limit access to additional information, build in additional hurdles to access. For instance, an intake team doesn’t necessarily need access to a complete patient file or diagnostic information. Each increase in the level of access should bring an increase in the security measures in place to protect the data in question.
|
| Educate employees | Employee education should take the form of regular trainings and updates on current information. This education should include not only best practices, but also current risks. For instance, if a new threat is identified within a certain sector, don’t simply ensure that your protocols are up to date. You should also ensure that anyone who may encounter the threat is aware of it. Information should be regularly disseminated as needed. |
| Enforce security measures | Having a data security plan is, of course, meaningless if it is not being enforced. Ensuring that data practices are adhered to at all times is essential. Like a pop quiz, some protocol audits should be spontaneous and unexpected. |
| Create plans | There are two key plans that need to be devised when thinking about data security and preventing data breaches: (1) a response plan and (2) an implementation plan that considers all potential outcomes. In building a response plan, you need to have a detailed and well-practiced plan in place in the event that a data emergency occurs. This type of planning can mitigate the worst possible outcomes. In building an implementation plan, whenever your company brings on new contracts, subcontractors, third-party entities, software, hardware, sectors, suppliers, etc., you need to analyze what can go right and what can go wrong prior to implementing any changes. By accounting for all outcomes (wanted and unwanted), you can be prepared to fix problems with speed and efficiency. |
| Update, update, update | This applies to each of the above factors. Update software, hardware, plans, training, security measures, access restrictions, etc. Again- when it comes to preventing data breaches, the most important thing is embracing the evolutionary and ever-changing landscape of data security. |
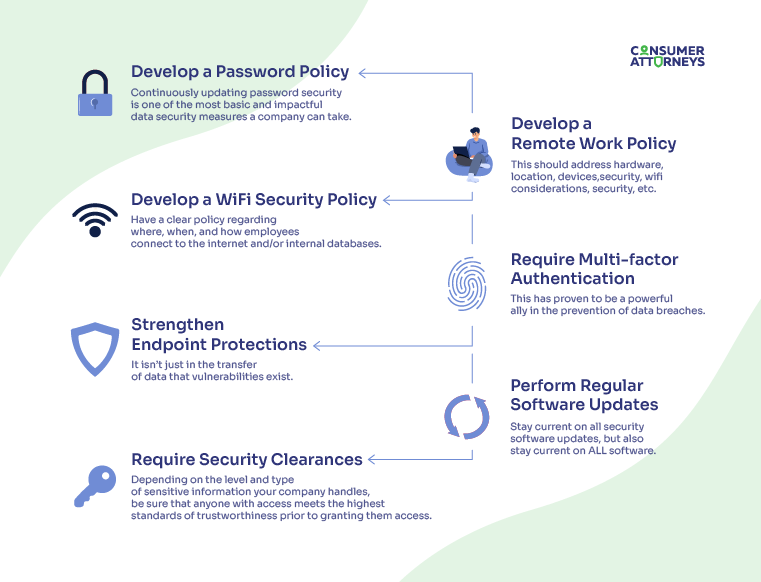
Best practices to prevent a data breach
On a slightly more specific level, there are a few best practices to consider when staying current on how to prevent a data breach. By developing and implementing ever-fresh policies around these considerations, your company’s preventative data breach measures should be strong.
One country that has recently stepped up its data privacy and protection game is India. With the passage of the Digital Personal Data Protection Act, companies operating in the e-commerce space in India (and other sectors, as well) will have to adhere to the rules established under this regulation. Preparing for a new era in data privacy and protection.
So, the best practices for keeping data where it belongs begin and end with preparation. First you have to know (say up to date on password protections, security measures, software updates, tech news, etc.). Then you have to plan (build a top-down strategy of policies and procedures to protect your data). And finally, you have to act (disseminate your knowledge, hold trainings, make roles clear and easy to understand, implement protocols, enforce policies).
Data breaches may be inevitable, but there is clear evidence that a well-executed approach can fortify your data against intrusion and build a wall of protection against leaky data vulnerabilities.
Ways to prevent a data breach
Perhaps not surprisingly, the best ways to prevent a data breach as a company are also very applicable to an individual looking to prevent a smaller-scale data breach (also known as identity theft). So, implement the same strategies, have the same game plan, stay current, and be prated.
Which of the following can be a log data source for investigating a security breach?
- Servers
- Firewalls
- Routers
- Applications
- Databases
- Switches
- Intrusion Protection Systems (IPSs)
Answer: All of the above!
This is because a log data source is basically what it sounds like- a data source that logs information in real-time. In other words, while in use, it is actively creating an event log. This is useful in two primary ways. First, by tracking events with this type of immediate, up-to-the-moment precision, you can be alerted to any potential threats. Second, by maintaining a log, you can collect data and insight into vulnerabilities and threats.
How Can You Prevent a Data Breach
In our current technological era, where business, banking, investing, government portals, utilities, education hubs, and every other imaginable consumer-facing platform is available online, it is not possible to 100% prevent a data breach. To some extent data breaches are a fact of life at this point, the inevitability of which is determined by little more than the statistical probability that you’ll be caught up in one type or another at any given point.
Having said that, it is not an entirely hopeless scenario. There are still things you can do on a person level to protect the data that is within your sphere of control and there are things you can do on if and when you’re data is compromised through a large-scale corporate or agency breach.
As an individual, you can prevent a breach of your own personal data on your network by implementing best practices for wireless, online, and mobile security. Review some of our suggestions and best practices above under “Best Practices to Prevent a Data Breach.” And in the meantime, consider what you should do if your personal information is compromised.
What to do if your personal information has been compromised
If you are an individual and your personal information has been compromised through a corporate, organizational, or agency data breach, you should do the following:
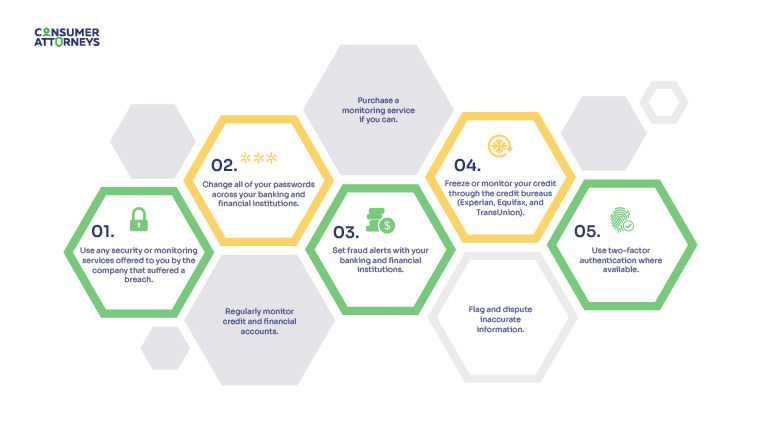
- Take advantage of any security offers made by the responsible party. This can include things like paid subscriptions to data security or monitoring services for several months of years.
- Change all of your passwords immediately, and use best practices for generating passwords. For instance, don’t use names of family members, birthdates, or other identifying information, make sure they meet the optimal password strength requirements, don’t reuse passwords on different sites or over different periods of time, etc.
- Set fraud alerts with your banking and financial institutions.
- Freeze or monitor your credit through the credit bureaus (Experian, Equifax, and TransUnion).
- Subscribe to a high-quality, real-time identity theft protection plan or monitoring service (if you aren’t offered a subscription by the responsible party).
- Take advantage of every single opportunity to enable two-factor authentication or other leveled-up security measures (like biometric security features).
- Stay informed about every single account you have out in the wide world of e-commerce. Do things like regularly monitor your credit reports, your financial statements, and your banking, retirement, and investment accounts. Have store accounts or store cards you don’t use? Close them down.
- Flag, investigate, and dispute anything that seems suspicious or is blatantly inaccurate, misleading, or false.
- Work with a consumer protection attorney at any point in this process to protect yourself. This is exactly the type of scenario they are trained and experienced in.
If you are a business, organization, or agency and your sensitive or private databases have been compromised through a data breach (whether internal, external, intentional, or accidental), begin by submitting a data security breach notification to the appropriate agency and to your consumer base.
For instance, the State of California Department of Justice requires that a data breach involving 500 or more customers must be logged with the state by filling out an online form and submitting necessary documentation, including communications sent to the impacted consumers.
On-line form to Submit Data Security Breach notification This information becomes a great resource for consumers, who can search the state database to see whether any of the companies they do business with have suffered a data breach.
Strategies to prevent a data breach
The best strategies to prevent a data breach involve staying current on what’s going on with your own data, what’s happening in the world of e-commerce generally, and what’s happening with the technology and security that impacts your life.
| Do this! | Why it Matters. |
|---|---|
| Know Your Own Data | It cannot be stressed enough that the single most important thing you can do as a consumer to help prevent a data breach or identity theft scenario is to stay aware of the activity and information available in every single one of your accounts. We are long past the point when people can get away with remaining somewhat oblivious to what’s going on in their accounts and still stay safe. You should be regularly and diligently checking your credit reports, bank accounts, investment and retirement accounts, retail accounts, benefits accounts, etc. If you encounter anything that doesn’t make sense or seem right, follow up on it. Investigate, make inquiries, track down an explanation that satisfies your concern. If you don’t get one, dispute it. If a dispute isn’t successful, get a lawyer. |
| Know What’s Going on in the Consumer Data Industry | Stay informed about the news around consumer data issues. If a company suffers a data breach, whether it impacts you directly or not, read about it. Be aware. Fill out and grow your understanding of how these breaches happen, get investigated, and get resolved. If new tactics and strategies are discussed, implement them across your own financial and credit portfolio. |
| Know What’s Going on in the Digital Security Industry | These areas are constantly evolving. When new tech-based of security features arise, or new protective software or hardware options are made available, say curious and attuned and do your research. Adopt any new standards or practices that genuinely level up your security game. The more in-the-know you remain on an ongoing basis, the better off you’ll be when it comes to preventing data incursion issues, and the better off you’ll be in managing a data breach if it happens to you. |
Steps to prevent a data breach
When it comes time to drill down to the specific steps to prevent a data breach, how you prepare will depend on whether you are acting as an individual or a business. We discuss the steps for both in greater detail above.
How to Stop a Data Breach
If you haven’t been able to prevent a data breach, the next best thing to do is immediately jump into action with a well-conceived plan for how to stop a data breach. By this we mean, how to stop it dead in its tracks and mitigate the damage it can cause before it upends your financial life completely.
If you learn that your personal information is, or likely is, involved in a data breach, do the following:
- Stay connected to the communications coming from the company involved and the information available in the news, and immediately implement any steps that you are advised to take.
- Change and update passwords across all of your platforms, including any banking, finance, investment, retirement, credit, utility, government, and other accounts. It’s a pain, yes. But it’s the most critical step you can take. And be sure to devise the strongest passwords possible.
- Take advantage of any additional security measures offered, if you haven’t already. For instance, if a company offers two-factor authentication and you haven’t yet opted in, now is the time. Does it slightly slow your log-in process for certain sites? Yes. But it exponentially increases your security and we think the trade-off is worth it.
- Use the strategies to prevent data breach that we discuss above.
What type of information is the most frequently exposed in a data breach?
While any information can be exposed in a data breach, it will not come as a surprise to learn that financial information is the most frequently exposed. It’s easy to imagine why. For instance, a hacker or criminal network can access diagnostic information from hospitals, which can still be horrifically traumatic for patients. But typically, even when hackers target hospitals, what they’re really looking for is personal data that can be paired with any other personal data about a person so that unauthorized access can be gained into their financial portfolio.
So, information about credit cards, bank accounts, investment funds, etc. are the most frequently exposed. Other top contenders are social security numbers, passwords, addresses and phone numbers, email addresses, drivers’ license details, medical data, and online activity data (such as the info tracked across social media platforms).
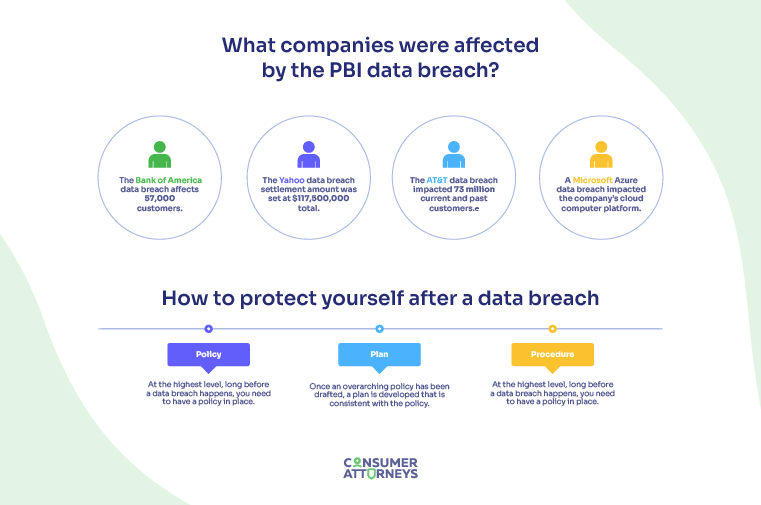
Who were affected by the PBI data breach?
The PBI data breach affected Bank of America and other companies on a massive global scare such as Shell, Siemens Energy, Continental Casualty Company (CNA), First Merchants Bank, TransAmerica LIfe Insurance Company, Fidelity, Genworth Financial, CalPERS, the Teachers Insurance and Annuity Association of America, the Virginia Retirement System, Schneider Electric, City National Bank, and federal agencies including the Department of Energy, Department of Agriculture, and Department of Health and Human Services, among others.
The PBI data breach involved a large cybercriminal network called Clop, widely known to be an active Russian-speaking ransomware gang. One of the Clop’s primary strategies is to find a way to hack into a software program in use with a large number of companies. Once Clop is able to breach the security of this software, it gains access to the sensitive databases of any company that is currently using the software, which it then holds for ransom. In this case, Clop exploited a security lapse in the MOVEit software, which PBI or Pension Benefit Information LLC, uses. And since PBI is itself a company that provides serves to other companies, each and every one of its client companies was also caught up in the ransomware scheme. Since PBI provides data gathering and vetting services to large companies such as insurance companies, state retirement plans, and others, the data at risk within these companies is of the highest sensitivity.
There were multiple PBI data breach lawsuits filed following this massive breach. Anyone who has been impacted can reach out to a consumer protection law firm, such as Consumer Attorneys to assess their options.
Other Big Data Breaches
How much can individuals sue companies for in the event of a data breach?
There is no one-size fits all answer to this question. In fact, even though claimants may join a class action lawsuit, within that group of injured consumers, if a settlement is reached, some claimants may be entitled to larger payouts than others. The specifics of determining who gets what dollar amount can be shaped by factors such as the extent of the harm suffered.
For instance, if one claimant was caught up in the breach to the extent that they had to take burdensome actions (such as change passwords and monitor accounts) but another claimant suffered concrete identity theft as a result, the latter clearly represents an overall greater harm endured. For this reason, some claimants in a class action come away with nominal amounts (less than $100 up to several hundred dollars) and others come away with significant amounts (thousands or tens of thousands of dollars).
Which of the following is not a risk to a company or its employees as a result of a data breach?
A. Diminished consumer trust
B. Regulatory fines, lawsuit settlements, or legal consequences
C. Reputational or brand damage
D. Easy, low-cost monetary fixes
E. Identity theft
F. Business disruptions
If you guessed D, you are correct. Generally speaking, the clean-up following a data breach is an absolutely enormous, cumbersome, and expensive task. Depending on the size of the company, the scale of the breach, and the extent of the damages, the consequences can be absolutely detrimental from an economic standpoint.
How was Pensacola better prepared for a data breach than New Orleans?
Both Pensacola and New Orleans were hit with cyber attacks, but some security experts opined that Pensacola did a better job of managing the aftermath and fall-out from its attack. Some of the things cited were the fact that Pensacola had a strong cyber-attack/data breach protocol in place, conducted regular trainings with key personnel, and had a strong and prepared communications strategy. This combination of proactive factors gave Pensacola a head start in mitigating damages, spearheading a recovery operation, and engendering employee trust.
Alternatively, some saw New Orleans’ response as more reactive in nature, which signaled a lack of comprehensive preparation in advance.
Perhaps not surprisingly, when dealing with data breaches and the fallout that ensues, it does matter which state you reside in and what the laws say about your rights to information and recourse. Let’s take a look at the laws of California and New York, below.
California data breach notification law
A state like California leans into the consumer-facing side of these types of data breaches, emphasizing risk mitigation and communication when addressing the harms. You can see this primarily through the notice requirements and the enormous, searchable catalog of notices that California maintains. Both private businesses and state/local agencies must notify any “California resident whose unencrypted personal information…was acquired, or reasonably believed to have been acquired, by an unauthorized person.” California data breach notification law
In addition, any notice that gets sent to greater than 500 residents must “be provided to the California Attorney General” and is made available online in a database of notices that residents can search.
New York data breach notification law
In New York state, any businesses or persons “who own or license computerized data which includes private information must disclose any breach of the data to New York residents whose private information was exposed.” And, notices must also be provided to the state Attorney General, State Police, and the Department of State’s Division of Consumer Protection. If a state agency is the entity whose data was breached, it must also notify the state AG and Dept. of Consumer Protection. However, it must notify the state Office of Information Technology Services rather than the state police. New York data breach notification law.
But no matter where you live or do business, you should know the data breach laws of your state. According to the National Conference of State Legislatures, as of 2022, all U.S. states, the District of Columbia, Guam, Puerto Rico, and the U.S. Virgin Islands “have security breach notification laws that require businesses or governments to notify consumers or citizens if their personal information is breached.”
What data breach just happened?
Unfortunately, massive data breaches are becoming a fairly regular occurrence, but one of the biggest and most impactful recently targeted Ticketmaster. In May of 2024, personal data from 560 million Ticketmaster customers was stolen and exploited on the dark web.
How to Protect Yourself After a Data Breach
As a business looking to mitigate damages and manage a response, the best way to protect yourself after a data breach is to follow the three steps outlined by the Department of Education, Privacy Technical Assistance Center. The three key steps are to (1) devise a policy, (2) make a plan, (3) know the procedure. Data Breach Response Checklist
- Policy: At the highest level, long before a data breach happens, you need to have a policy in place. This includes creating a vision, goals, scope, priorities, etc. It should also include any necessary definitions, role considerations, “reporting, remediation, and feedback mechanisms.”
- Plan: Once an overarching policy has been drafted, a plan is developed that is consistent with the policy. This will be a “high-level strategy for implementing the data breach policy.” At this level, it will include an analysis of necessary resources and allocation of responsibilities.
- Procedure: This is the practical, tactical, hands-on strategy for implementing the plan. By developing and disseminating the plan, and training the necessary people in their functional roles, everyone will be prepared for eventual data breach.
IBM similarly recommends that you start from a place of knowledge when it comes to addressing data breaches. “The best way to prevent and respond to data breaches is to learn why and how they happen.” Data breach action guide
How to protect my identity after a data breach
As an individual looking to mitigate damages and recover from any exploitation of personal data, there are a few things you can do, which we go over in detail in other sections of this article. But the general gist is, you need to do this:
Security awareness training can reduce the risk of a data breach by what percentage?
Recent data indicates that security awareness training can reduce the risk of a data breach by up to 70%. While this type of training doesn’t eliminate risks in their entirety, it clearly mitigates vulnerabilities by a large margin. This is consistent with the overall theme of preventing or recovering from data breaches- knowledge, know-how, and training are everything! Be prepared to stop threats and be prepared to recover from attacks.
Keep in mind that a decrease of risk by 70% is hugely important when considered in light of the average cost of cleaning up after a data breach, which is 4.88 million dollars so far in 2024. Cost of a Data Breach Report 2024 This continues the trend of seeing an increase in the average global cost of a data breach, globally, year over year.
What is the difference between cyber insurance and data breach insurance?
While they are similar and fall within the same general category of insurance, there are two key differences between cyber insurance and data breach insurance. But before we get into that, it is helpful to know that cyber insurance is also referred to as cyber liability insurance. You’ll see that the liability aspect is an important distinction.
- Data breach insurance is intended for small businesses and is aimed at helping those businesses afford some of the procedural aspects of recovering from a data breach. This includes things like notifying the people impacted by the breach (employees, clients, patients, etc.), providing monitoring services, hiring communications teams or PR firms to help disseminate information or convey a message, notifying governmental agencies (if necessary), etc. Like all insurance, data breach insurance cost can vary depending on the size and scale of your small operation, and the types of coverages you’re looking for, so shop around. Most major insurance providers have offerings, with some building coverage packages for around $25/month.
- Cyber liability insurance is intended for large businesses and has a dual goal. First, just as with data breach insurance, it affords coverage meant to ease the burden of the procedural aspects of recovering from a data breach (see above). Second, it covers liability arising out of data breaches. This is what really distinguishes it from data breach insurance. Liability coverage includes costs associated with things like extortion payments, lawsuits, fines, etc.
Who Can Help You Recover from a Data Breach?
Consumer Attorneys, the nation’s largest consumer reporting law firm, can help you recover from the harmful impact of a data breach.
The fall-out of a data breach (or many, many data breaches) for consumers is that eventually their personal data may end up on the dark web, sold to known cybercriminals, or otherwise exploited. When a data breach transforms into the unauthorized use of your personal information, now you’re into identity theft and identity fraud territory. And when this happens, financial havoc typically follows.
Financial portfolios (banking, investment, retirement), benefits, insurance, retail accounts, utitlity accounts, contracts (rental agreements), loans (car financing), etc., can all be falsely transacted in your name or impacted by fraudulent activity. When this happens, some consumers may have recourse through the criminal justice system, but many times, the perpetrator is never found. And even worse, whether or not someone faces consequences for exploiting your finances and causing you genuine emotional and mental trauma, the false data that gets generated by unauthorized activities frequently ends up all over your credit and financial reports, and is very difficult to clean up and recover from.
If you need help getting the impact of data breach related identity fraud, or any other form of identity theft or fraud, removed from your credit reports and other financial accounts, we can help. With over 75 years of combined practice experience, we have helped thousands of consumers recover from these situations, and we can help you, too.
Contact us today to learn more. Our consultations and representation cost you zero out-of-pocket because the reporting companies pay our legal fees when we settle or win.
Frequently Asked Questions
All-out preventing a data leak is a challenging and nearly impossible task, though risks can be mitigated substantially with the right preparation. But stopping a data leak in its tracks is doable. The most effective steps to stop a data leak are- (1) Be aware of it in the first place! This may seem like a no-brainer, but many leaks go unrecognized for years. Be diligent about running updates, running simulations to look for problems, and staying on top of current tech and data news. Let nothing slip through the cracks or get put off for another day. (2) Make a plan, train for your plan, and implement your plan when the time comes. When everyone understands their role, what needs to happen, and how to make it happen, you can act quickly and seamlessly to put an end to a data intrusion. Note that preparation is everything when it comes to data breaches! Prepare with knowledge and a well-rehearsed plan of action.
Leak-Lookup is exactly what it sounds like- a searchable database of businesses impacted by data leaks. However, it is a paid service, so users must sign up for an account and purchase a plan, which then gives them access to the database containing information from over 4,000 data breach incidents and counting. The site purports to have information on over 26,000,000,000 records! Ironically, Leak-Lookup itself was involved in a data breach of its own in January 2024, wreaking wide and devastating data havoc.
The seven principles of GDPR are (1) accountability, (2) accuracy, (3) lawfulness, fairness, and transparency, (4) purpose limitation, (5) data minimization, (6) storage limitation, (7) integrity and confidentiality. The General Data Protection Regulation (GDPR) is a law passed by the European Union that sets strict regulations and expectations about how personal data is gathered, stored, processed, transferred, and used in the EU. While it technically only applies to residents of EU countries, it has a broader global impact because any business entity seeking to engage with EU residents through e-commerce and consumer data collection practices must abide by this regulation and guidance.

Daniel Cohen is the Founder of Consumer Attorneys. Daniel manages the firm’s branding, marketing, client intake and business development efforts. Since 2017, he is a member of the National Association of Consumer Advocates and the National Consumer Law Center. Mr. Cohen is a nationally-recognized practitioner of consumer protection law. He has a we... Read more
Related Articles




R
ONGS™You pay nothing. The law makes them pay.







